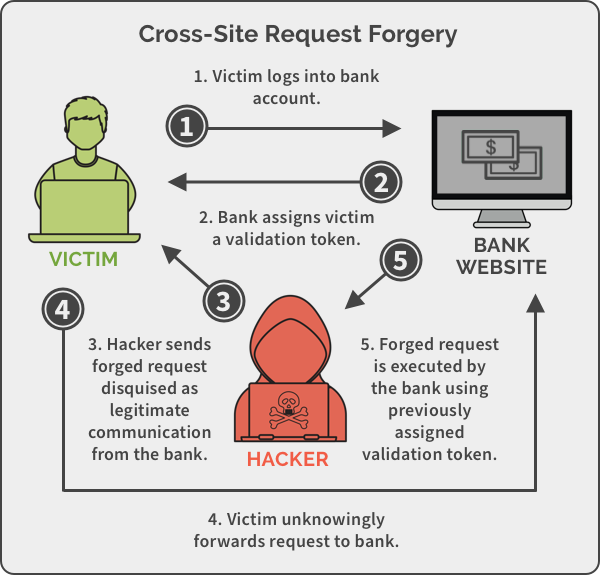
Cross-Site Request Forgery CSRF
I found this image is best visual explanation of what the CSRF is spanning.com/blog/cross-site-forgery-web-based-application-security-part-2/
Consider that you get an email from mybank. It has a 1×1 tiny image pixel with the code below.
If you’re logged into your mybank account and your browser loads images, it will lead to a bank transfer of $100 into the hacker’s account, without any visible indication such as the link opening in a new window.
This is an example of using CSRF to exploit mybank.com’s GET request to transfer parameters and execute actions. Similarly, other HTTP requests such as POST, PUT or DELETE can also be hacked.
This is an example of using CSRF to exploit mybank.com’s GET request to transfer parameters and execute actions. Similarly, other HTTP requests such as POST, PUT or DELETE can also be hacked.
Anti-CSRF TokensThe most common way of preventing a CSRF vulnerability is Token Based Mitigation, known as anti-CSRF or synchronizer tokens. It is a cryptographically secure token added as a hidden field on forms. The anti-CSRF token is then included in any authenticated state-changing request that requires a cookie. The web app only accepts the request if the token is validated. As the token is in a hidden field and is randomly generated every time the page is served, it secures the web app against CSRF attacks.